- Cybersecurity experts have identified significant security flaws in SAP’s AI Core platform.
- Termed SAPwned by Wiz, these vulnerabilities could expose sensitive customer data and access tokens.
- The weaknesses could lead to unauthorized access to private assets in AWS, Microsoft Azure, and SAP HANA Cloud.
- Attackers could alter Docker images and disrupt artifacts, causing potential supply chain attacks.
- Vulnerabilities could grant cluster administrator privileges on SAP AI Core’s Kubernetes cluster.
- The issues stem from inadequate isolation and sandboxing mechanisms in the platform.
- Netskope reports increased enterprise use of generative AI, prompting enhanced risk mitigation strategies.
- The rise of the NullBulge cybercriminal group, targeting AI and gaming sectors, highlights ongoing threats.
Main AI News:
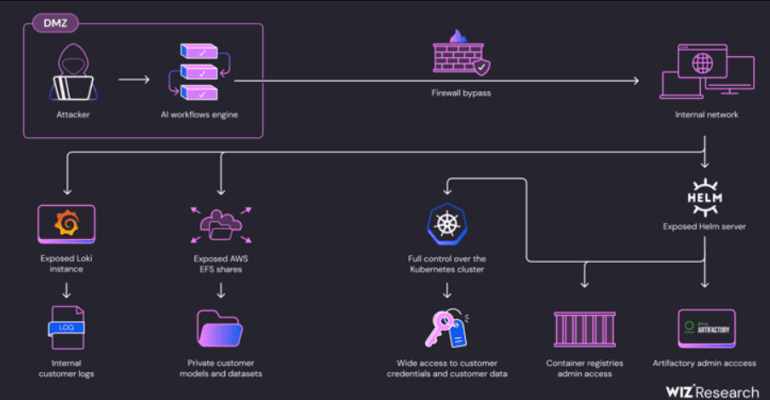
Cybersecurity experts have identified critical security flaws in SAP’s AI Core platform, which is designed for crafting and deploying predictive AI workflows. These vulnerabilities could potentially expose sensitive customer data and access tokens. Termed SAPwned by cloud security firm Wiz, the issues encompass five key vulnerabilities.
“The flaws we discovered could have enabled attackers to compromise customer data and corrupt internal artifacts, leading to contamination of interconnected services and other clients’ environments,” reported security researcher Hillai Ben-Sasson in an exclusive interview with The Hacker News. Following a responsible disclosure on January 25, 2024, SAP addressed these vulnerabilities by May 15, 2024.
The identified weaknesses could facilitate unauthorized access to customers’ private assets and credentials in cloud platforms like AWS, Microsoft Azure, and SAP HANA Cloud. Additionally, attackers could alter Docker images on SAP’s internal and Google Container Registries and disrupt artifacts hosted on SAP’s internal Artifactory server, leading to potential supply chain attacks on SAP AI Core services.
Furthermore, the vulnerabilities could grant attackers cluster administrator privileges on SAP AI Core’s Kubernetes cluster, exploiting the exposed Helm package manager server for both read and write operations. “With this access level, attackers could directly access other customers’ Pods, exfiltrate sensitive data such as models and datasets, and manipulate models’ inference,” Ben-Sasson explained.
Wiz attributed these issues to the platform’s lack of effective isolation and sandboxing mechanisms, which enable malicious AI models and training procedures to operate without proper containment. “Recent security flaws in AI service providers like Hugging Face, Replicate, and SAP AI Core underscore significant gaps in tenant isolation and segmentation,” Ben-Sasson noted. “Newer services often rely on containerization, which offers less robust security compared to traditional cloud providers’ virtual machines.“
An attacker could exploit these vulnerabilities to create a standard AI application on SAP AI Core, bypass network restrictions, and probe Kubernetes Pod internals to extract AWS tokens and access sensitive customer data. “AI models are essentially code. Running untrusted AI models on your infrastructure exposes you to potential supply chain attacks,” Ben-Sasson warned.
Netskope’s latest report indicates that growing enterprise adoption of generative AI has led organizations to implement blocking controls, data loss prevention (DLP) tools, and real-time coaching to mitigate risks. “Regulated data, which organizations are legally obligated to protect, constitutes over a third of the sensitive data shared with generative AI applications, posing a significant breach risk,” the company reported.
The findings also coincide with the rise of a new cybercriminal group, NullBulge, which has targeted AI and gaming entities since April 2024. This group is known for stealing sensitive data and selling compromised OpenAI API keys on underground forums while masquerading as a hacktivist collective “protecting artists against AI.” “NullBulge targets the software supply chain, weaponizing publicly available code and mod packs to introduce malicious libraries,” said SentinelOne security researcher Jim Walter. “This group exemplifies the ongoing threat of low-barrier ransomware and persistent info-stealer infections.”
Conclusion:
The exposure of critical vulnerabilities in SAP AI Core underscores a growing concern for enterprise security, particularly within AI and cloud-based platforms. The identified flaws not only jeopardize sensitive customer data but also raise the risk of significant supply chain attacks. As generative AI becomes more prevalent, organizations must enhance their security measures and adopt robust isolation practices to safeguard against emerging threats. The rise of groups like NullBulge further emphasizes the need for vigilance and proactive risk management in the evolving cybersecurity landscape.