TL;DR:
- NetRise introduces Trace for XIoT security, employing AI-powered semantic search.
- Trace enables intent-driven searches, moving beyond traditional signature-based methods.
- It covers a broader range of vulnerabilities, misconfigurations, and flaws.
- The CTO sees it as a significant advance in product security.
- It revolutionizes asset discovery and resolution using AI.
- Features include AI-powered search, supply chain introspection, and LLM-based validation.
- Trace helps organizations trace affected assets with a single query, eliminating redundancy.
Main AI News:
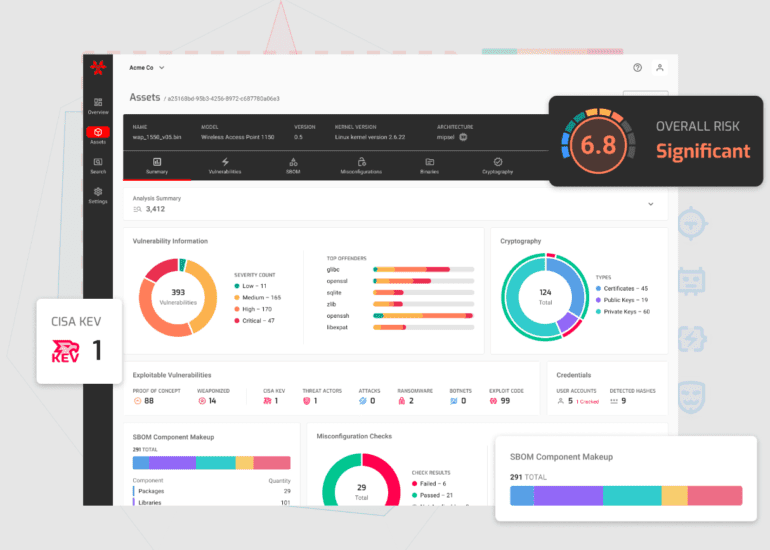
In a groundbreaking move within the realm of Extended Internet of Things (XIoT) security, NetRise is proud to introduce Trace, a cutting-edge solution designed to identify and validate compromised and vulnerable assets spanning firmware and cyber-physical systems. Launched on November 9, 2023, as part of the NetRise Platform, Trace marks a historic milestone by harnessing the power of AI-driven semantic search to empower users to scrutinize their assets like never before.
Traditional signature-based search methodologies are a thing of the past. With Trace’s intent-driven searches, users can delve into their systems based on the underlying motives or intentions behind the code and configurations leading to vulnerabilities. This revolutionary approach expands the scope to encompass a wide array of software packages, misconfigurations, and unidentified flaws. It eloquently presents the affected assets, files, and packages in plain natural language, while also mapping their intricate relationships throughout the entire supply chain. The result? An eradication of the need for cumbersome scanning mechanisms.
Michael Scott, the CTO of NetRise, expressed the significance of this release, particularly in the challenging landscape of XIoT device and component identification. He described it as a “significant advancement in product security” that promises to streamline the detection and resolution of issues within complex systems. Notably, it redefines how NetRise’s clientele approaches problem discovery and resolution, with AI emerging as the linchpin in streamlining processes.
Trace combines the prowess of AI-driven semantic search, supply chain impact analysis, and vulnerability validation powered by Large Language Models (LLMs). This integration creates an all-encompassing and potent solution for detecting threats, be they well-known or concealed, lurking within low-level firmware and other cyber-physical systems.
Key features and capabilities of Trace include its AI-powered search function, which enables users to uncover vulnerabilities across their entire asset spectrum through semantic search. It goes beyond this, offering deep introspection into supply chains and tracing the origin of code, thus unearthing potential risks tied to third-party or proprietary software packages. Additionally, it boasts LLM-based vulnerability discovery and validation, identifying vulnerabilities and assessing their impact using either code-based or natural language queries across an organization’s firmware, software, and cyber-physical systems.
In a world grappling with an uptick in supply chain compromises, both public and private sector industries are on a quest to pinpoint assets, devices, and software harboring compromised elements and vulnerabilities. The challenge is compounded when scrutinizing device firmware and build artifacts. Enter Trace—a game-changer.
NetRise empowers organizations with Trace, enabling them to trace all affected assets with a single query. Upon finding a positive match, it generates a comprehensive graph showcasing the interconnected software supply chain components. This eliminates the need for repetitive scans or asset reprocessing, a crucial time-saving measure in discerning the full spectrum of threats—from nation-state actors to inherent vulnerabilities and subpar development practices—across devices, firmware, and software packages.
Conclusion:
NetRise’s Trace, with its innovative AI-powered search capabilities, marks a pivotal moment in XIoT security. This disruptive solution not only streamlines vulnerability detection but also transforms how businesses approach security challenges. It empowers organizations to swiftly identify and address threats, enhancing the overall resilience of the market to evolving cyber risks.