TL;DR:
- Google reveals its dedicated ethical hacker team to ensure AI safety.
- The Red Team identifies six common attack vectors targeting AI systems.
- Attacks include prompt engineering, training data extraction, backdooring the model, adversarial examples, data poisoning, and exfiltration.
- Google emphasizes the importance of red teaming in product development and research to counter potential threats.
- Implementing robust security measures can mitigate risks and protect AI systems.
Main AI News:
As the world embraces the potential of artificial intelligence (AI), concerns regarding its security risks have escalated. Acknowledging the significance of cautious AI implementation, Google, a frontrunner in next-gen AI, has taken a decisive step in ensuring AI safety. In a recent blog post, the tech giant introduced its ethical hacker team, dedicated to combating potential threats. This revelation marks the first time Google has publicly disclosed such crucial information.
Founded approximately a decade ago, Google’s Red Team has been diligently working to identify risks within the rapidly evolving AI landscape, particularly focusing on large language models (LLMs) powering generative AI systems like ChatGPT and Google Bard. Their findings have unveiled six common attack vectors, each possessing a unique level of complexity.
The first type of frequent assault identified by Google is “prompt attacks,” leveraging “prompt engineering” to provide LLMs with specific instructions for tasks. When exploited maliciously, this approach can deliberately influence the output of an LLM-based application in unintended ways.
Another menacing attack is “training data extraction,” seeking to replicate precise training instances used by an LLM, often containing sensitive information. Attackers are incentivized to target personalized models or those trained on data containing personally identifying information (PII), thereby gaining access to valuable data like passwords.
“Backdooring the model” is a third attack method, where an attacker clandestinely modifies a model’s behavior to produce inaccurate outputs triggered by specific phrases or features. This concealed code within the model or its output can lead to harmful consequences.
The fourth attack, known as “adversarial examples,” involves inputs intentionally given to a model, resulting in highly unexpected outputs while appearing innocuous to the human eye. The impact of successful adversarial examples can range from insignificant to critical, depending on the AI classifier’s use case.
For software developers relying on AI to aid in their work, “data poisoning” attacks can manipulate the model’s training data to influence its output, posing threats similar to backdooring the model and jeopardizing the software supply chain.
The last recognized attack is “Exfiltration,” where attackers steal the file representation of a model, enabling them to access crucial intellectual property. This pilfered data can be utilized to create custom-crafted assaults, giving attackers an edge in their endeavors.
To counter such attacks, Google advises businesses to employ red teaming in their work processes, supporting product development and research efforts. Additionally, implementing robust security measures to secure AI models and systems can significantly reduce the risk of potential attacks.
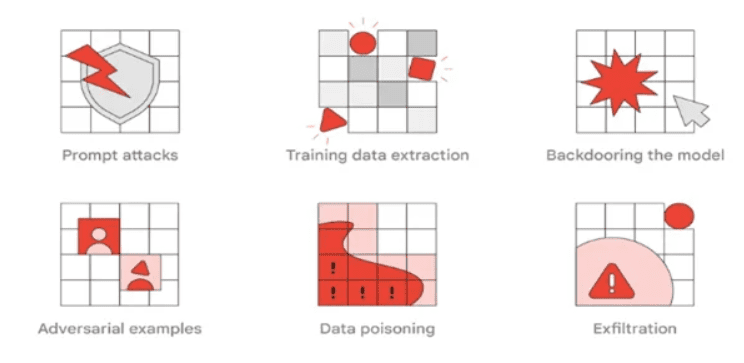
Types of Red Team Attacks on AI Systems. Source : Google
Conclusion:
Google’s proactive approach to addressing the security risks associated with AI through its Red Team is commendable. By unveiling common attack vectors and advocating for red teaming in the development process, Google aims to bolster AI system resilience and protect against malicious activities. This heightened focus on AI safety sets a precedent for the market, urging other companies to prioritize security measures and maintain the trust of users and businesses relying on AI technologies. As the AI market continues to grow, a strong emphasis on vigilance and proactive defense will be crucial to building a sustainable and secure AI ecosystem.

