- Demand for vCISO services is rising due to increasing third-party risks, regulatory demands, and cyber insurance requirements.
- Cynomi, an AI-driven vCISO platform, addresses the need by offering tailored security and compliance solutions.
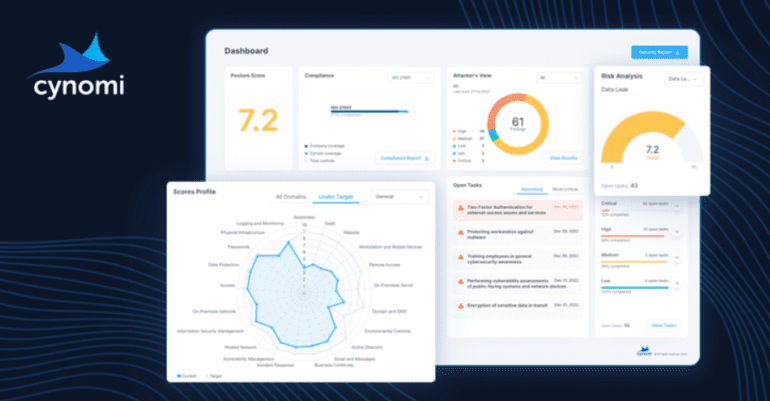
- Features include automated security assessments, gap analysis, compliance readiness, policy creation, and task management.
- Multi-tenancy support enables scalable client management for MSPs and MSSPs.
- Onboarding questionnaires gather client information for tailored remediation plans.
- Internal and external scans provide comprehensive insights into client cyber profiles.
- Continuous security assessment ensures proactive defense against evolving threats.
- Tailor-made security policies and actionable remediation tasks streamline cybersecurity efforts.
Main AI News:
The surge in demand for vCISO services reflects the evolving landscape of cybersecurity challenges faced by SMBs and SMEs. These entities grapple with escalating third-party risks, stricter regulatory obligations, and more stringent cyber insurance prerequisites than ever before. Yet, the complexity of these demands often surpasses their internal capabilities and resources, necessitating the engagement of external expertise.
Enterprises in the Managed Service Provider (MSP) and Managed Security Service Provider (MSSP) realms are not immune to this predicament. The scarcity of cybersecurity talent has created a fiercely competitive environment where the costs of talent acquisition and retention are prohibitive. Moreover, the imperative to maintain proficiency in both security and compliance adds another layer of complexity to this equation.
Amidst these challenges, Cynomi emerges as a game-changer.
Cynomi, the pioneering AI-driven vCISO platform, offers a compelling solution. It empowers MSPs, MSSPs, and consulting firms to deliver vCISO services efficiently and effectively, thereby meeting the burgeoning demand without overstretching existing resources. Drawing inspiration from the expertise of leading CISOs worldwide, Cynomi equips enterprises and their clients with expert-level insights and tools tailored to their specific industry requirements.
At the core of Cynomi’s value proposition are its two primary vCISO pillars: security and compliance. Through an automated and actionable approach, Cynomi facilitates security assessments, conducts gap analyses, ensures compliance readiness, facilitates policy creation, streamlines task management, and provides comprehensive reporting capabilities. The result? Enhanced revenue streams, an expanded customer base, reduced risk assessment timelines, accelerated report generation cycles, well-structured processes, and shorter employee onboarding durations.
Facilitating Scalability and Management of Multi-Tenant Accounts
Cynomi’s design is inherently geared towards supporting multi-tenancy, with a particular focus on enabling partners to manage their client portfolios seamlessly. By creating and managing individual sub-accounts for each client, organizations can maintain granular oversight while granting clients access to the Cynomi platform. Delegating roles and ownership within the team for each client account enhances operational efficiency without compromising on administrative privileges. A unified account management interface further streamlines centralized oversight, allowing for swift user management actions such as profile editing, invitation resending, and account unblocking.
Building Comprehensive Cyber Profiles through Onboarding Questionnaires
Effective client onboarding begins with capturing essential information to tailor remediation plans accurately. Cynomi initiates this process with an onboarding questionnaire that elicits insights into the client’s infrastructure. Subsequent short follow-up questionnaires, generated based on the initial responses, delve deeper into specific aspects of the client’s security posture. The culmination of these questionnaires furnishes a holistic view of the client’s security landscape, enabling Cynomi to formulate bespoke policies that address identified gaps. Furthermore, the flexibility to revise questionnaires ensures alignment with evolving client environments, with corresponding updates seamlessly reflected in policy adjustments.
Augmenting Insight with Internal and External Scans
Cynomi enhances its understanding of client cyber profiles through comprehensive external and internal scans. External scanning encompasses the evaluation of externally exposed assets, including IP addresses and URLs, to identify vulnerabilities and assess configuration robustness. Meanwhile, internal scanning scrutinizes internal network assets such as active directories and endpoints to gauge security hygiene and configuration integrity. Additionally, Cynomi facilitates the integration of external scan data from popular security assessment tools such as NESSUS, Qualys, and Microsoft Secure Score, enriching the breadth and depth of its analysis. Scan findings are meticulously aggregated and linked to relevant tasks and policies, ensuring a cohesive remediation approach.
Continuous Security Assessment for Informed Decision-Making
Cynomi’s proactive approach to security assessment entails continuous evaluation against industry-specific standards, regulatory frameworks, and threat intelligence feeds. Leveraging insights from security questionnaires, scans, and dynamic cyber domain prioritization, Cynomi computes a comprehensive security posture score for each client. Criticality levels assigned to individual requirements underscore their significance in bolstering organizational security resilience. By quantifying risks such as ransomware and data breaches, Cynomi empowers stakeholders with actionable insights to fortify their defense mechanisms. A consolidated dashboard presents an at-a-glance overview of the client’s security posture evolution, incorporating metrics such as vulnerability analysis, risk scoring, remediation plans, and compliance adherence.
Crafting Tailor-Made Security Policies for Proactive Defense
Cynomi’s policy generation engine leverages decades of collective CISO expertise to craft bespoke security policies tailored to each client’s unique requirements. These policies encapsulate purpose, scope, and protection mandates in a user-friendly format, facilitating seamless comprehension and adherence. An intuitive interface empowers users to delve into policy specifics, including associated tasks and progress tracking, fostering transparency and accountability. By quantifying policy effectiveness through company-wide scoring, Cynomi facilitates informed decision-making and prioritization of remediation efforts.
Executing Actionable, Prioritized Remediation Tasks with Precision
The translation of policy requirements into actionable tasks lies at the heart of Cynomi’s remediation strategy. Drawing inspiration from industry-leading CISO insights, Cynomi curates a prioritized task list that aligns with organizational priorities and risk profiles. Task types encompass a spectrum of technical controls, administrative procedures, and security component configurations, ensuring comprehensive coverage of security domains. A user-friendly interface enables seamless task management, with filters and progress tracking functionalities enhancing operational efficiency. Detailed guidance and customizable task parameters empower users to implement controls effectively, while progress monitoring mechanisms facilitate real-time visibility into remediation status.
Conclusion:
The emergence of Cynomi as a pioneering vCISO platform signifies a paradigm shift in the cybersecurity landscape. By offering a comprehensive suite of AI-driven solutions tailored to industry-specific needs, Cynomi empowers organizations to navigate the complexities of modern cyber threats with confidence and efficiency. This innovation is poised to reshape the vCISO market, driving increased adoption and setting new standards for cybersecurity excellence among SMBs, SMEs, and MSPs alike.